
Linux Forensics
Linux Forensics
Essential Linux Forensics: Investigate, Analyze, Protect, and Secure.
In Partnership With:

In Partnership With:

Supporting Partner:
.png)
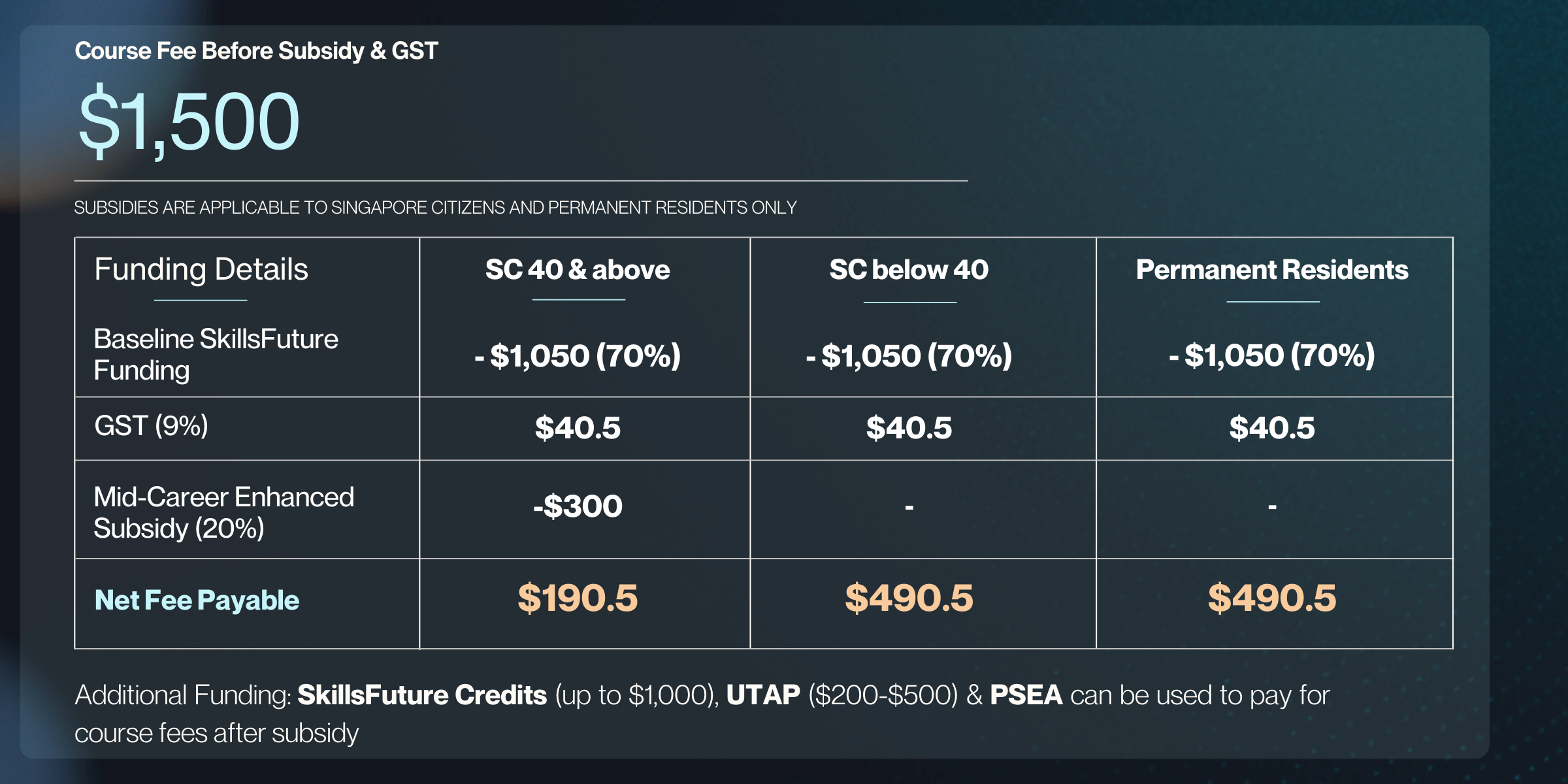
Course Fee
Full Course Fees
SG Citizen (aged 21-39) or PR
SG Citizen (aged 40 & above)
Full Fees
$19,500
$19,500
$19,500
SkillsFuture Funding
-
$13,650 (70% Subsidy)
$17,550 (90% Subsidy)
Total Nett Fee
$19,500
$5,850
$1,950
GST (9%)
$1,755
$526.5
$526.5
Total Fee Payable
$21,255
$6,376.50
$2,476.50
Additional Funding: SkillsFuture Credits (up to $1,000), UTAP ($200-$500) & PSEA can be used to pay for course fees after subsidy
Programme Fees & Funding
Learning Outcomes:
Participants will:
- Master Linux basics necessary for forensic tasks.
- Learn log and file analysis for forensic clues.
- Understand evidence collection and threat detection.
- Grasp network security and attack mitigation.
- Practice with forensic tools for evidence handling.
Question text goes here
- Become familiar with different attack scenarios
Course Syllabus:
Chapter 01
Linux Fundamentals
Intro to Linux
- Virtualization
- Basic Commands
- System Files
Services
- Installation
- Configuration Files
- Logs Files
Scripting
- File Permissions
- Linux Automation
Log Analysis
- Text Manipulation
- Built-in Logs
- Logs Best Practice
File Analysis
- Metadata
- Carving
- Steganography
- Calls
Network Analysis
- Wireshark
- General Network Tools
- TShark Automation
Chapter 02
Analysis
Question text goes here
- Become familiar with different attack scenarios
Artefacts
- Hashes and Encodings
- User Files
- Understanding Shells
- System Files
- Suspicious User-Info
Live Analysis
- Mounting Partitions
- Dumping Memory
- Cloning HDD
- Log File Advance Search
Captured Images
- Working with FTK
- Detecting Hidden Files and Directories
Chapter 03
Evidence Collection
Question text goes here
- Become familiar with different attack scenarios
Netcat
- Different Uses
Network Protocols
- MITM
- Analysing Traffic
Network Attacks
- SSH
- FTP
Hardening
Chapter 04
Cyber Security (Linux)
Question text goes here
- Become familiar with different attack scenarios
Chapter 05
Question text goes here
- Become familiar with different attack scenarios
Training Schedule:
Tailored To Client
Tailored To Client
Question text goes here
Training Methodology:
Apprenticeship-based Training
- Experience hands-on learning with our demonstration method on a virtual/host machine, ensuring immersive understanding.
- Our trainers prioritise showing over telling, explaining intricacies without relying on slides, offering direct engagement.
- Bridge your knowledge gap by connecting theoretical concepts to practical cybersecurity applications, enhancing career readiness.
Practice Labs
- Engage in repeated practice sessions to solidify and reinforce your understanding.
- Delve deeper with practice questions, encouraging students to explore interconnected topics and enhance comprehension.
- Stimulate critical thinking through challenge questions, prompting students to seek solutions and broaden their problem-solving abilities.
Assessment and Project
- Equip yourself with the expertise and tools essential for navigating corporate networks safely.
- Gain a comprehensive understanding of cyber-attacks to fortify your digital environment effectively.
- Broaden your horizon by familiarising yourself with diverse cyber-attack scenarios and their implications.
Question text goes here
- Become familiar with different attack scenarios
FAQs:
Question text goes here
- Become familiar with different attack scenarios
Quick Info
Programme Fee
Custom Pricing
Duration
5 Days (8 hours/day)
Schedule
Tailored To Client
Teacher-to-Student Ratio
1:30
Delivery Mode
On-site
View Course BrochureRegister NowBook Your SlotView BrochureView Brochure
Secure Your Future
Find out more about how we can help you secure your future in cybersecurity


.png)